
We’re excited to announce that Booth – metadata-secure video conferencing in a normal browser – is now available in open beta for free use: try it out at booth.video. We are also in closed beta of our enterprise offering that provides additional functionality.
What’s Wrong with Video Conferencing Today?
At INVISV, we believe you should have control over you and your organization’s data and shouldn’t have to sacrifice security and privacy to communicate with others. Unfortunately, your data is often intentionally aggregated, analyzed, and sold by some providers, and accidentally leaked or lost in data breaches. The few secure options that do exist are often difficult to set up and use.
The pandemic has accelerated the trend towards remote work and has made us more reliant upon third-party communications platforms. Conversations that used to be within the four walls of a conference room are now held in the cloud, on infrastructure that organizations do not own or have any control over. While the change to remote work has been hugely beneficial to many, it has turned organizations inside-out, handing over previously-private metadata and data in huge amounts.
Video conferencing is an essential, everyday tool for organizations today. But existing services provide little or no security. Every video call with today’s services leaves behind valuable information – the who, what, when, how, etc. of your call are all known to the service provider, often held by them in perpetuity, just waiting for a data breach. Most of the time, calls are not end-to-end encrypted: while calls are encrypted to the cloud provider, they can see and “listen in” on calls in real time or at a later date – and anyone who has hacked their systems can do the same.
We created Booth because when you meet your colleagues, you should know that your conversation is just that: your conversation.
Ask Your Video Conferencing Providers for INVISV Metadata Security and Privacy
INVISV’s goal is to take practical steps to ensure privacy for everyone. We do this by making it simple for existing services and apps to deliver real secure and private offerings. Booth is just one of many INVISV solutions for people-first privacy, all of which have been designed for integration with existing communications services.
Existing video conferencing providers can easily add Booth-style metadata protections. Contact us at booth@invisv.com to learn more.
What do Other Video Conferencing Services See?
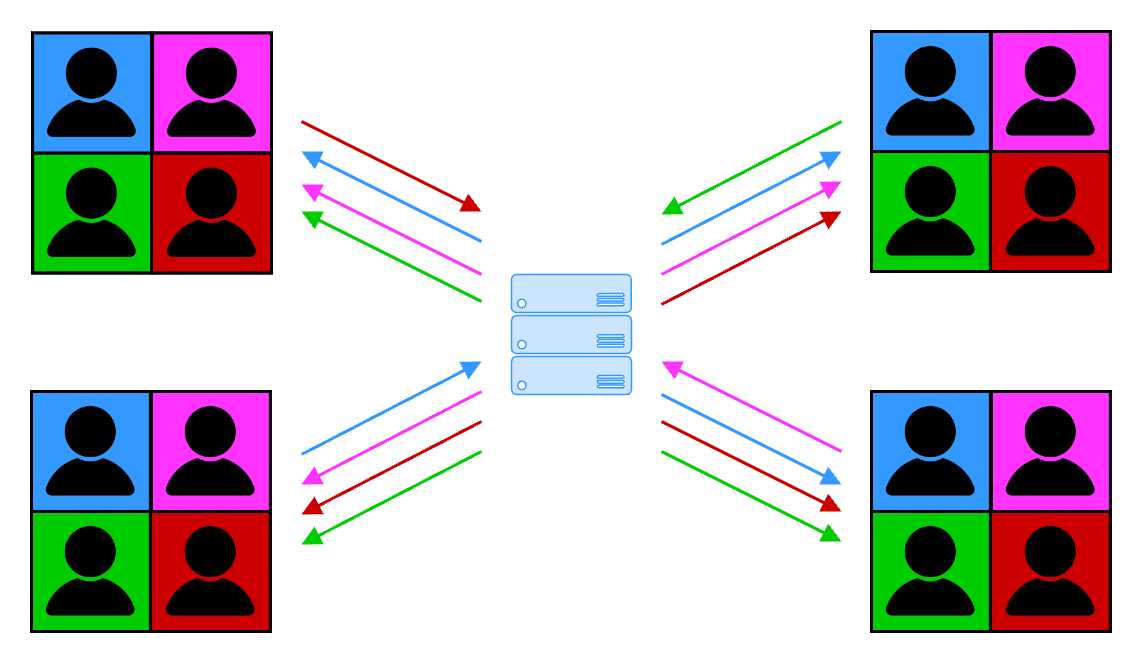
What happens when you use other video conferencing services? As shown in the diagram below, each user uploads a video stream to a video conferencing server that keeps track of each user in a meeting, and routes each user’s traffic to the group in the meeting. Their architecture allows the video conferencing platform to know precisely who is talking to whom, when, for how long. And, in most meetings end-to-end encryption is not enabled so the server and the company that runs it sees all the audio and video streams, chat, etc. of all participants in the meeting. This is even worse when cloud recording or transcription are enabled, as these services require the capture and processing of your conversation as raw, unencrypted data by the video conferencing service.
How Does Booth Protect You?
Booth leverages the same INVISV Multi-Party Relay (MPR) architecture that we also use to provide Internet privacy for Relay users. Using an MPR, users’ network identities (IP addresses) are masked from the cloud server that they connect to. In Booth, we partner with Fastly to provide decoupling without sacrificing performance, relying on their global footprint of high-speed network infrastructure. We designed Booth to not require special client software to use the MPR: Booth simply runs in your browser.
With Booth, users no longer connect directly to the video conferencing server, and instead connect through the MPR. The MPR masks the users’ network identities so that the server only sees traffic from the MPR servers with Fastly IP addresses.
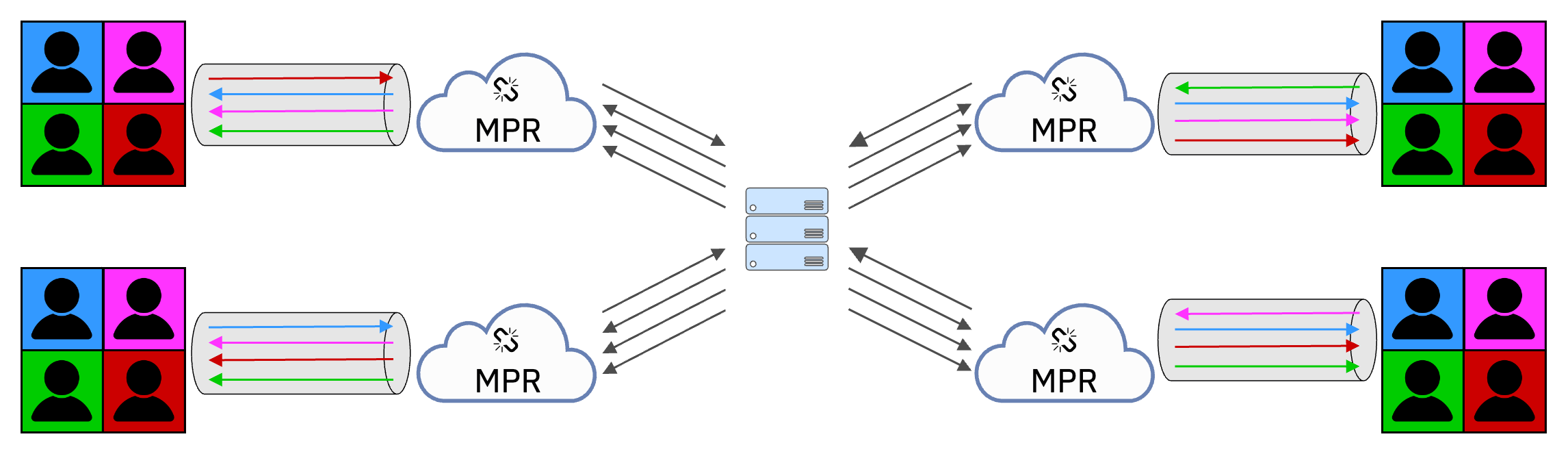
Booth is designed to use meeting “booths”, where the booth link is randomized for each meeting. Likewise, Booth users don’t need to reveal their names to the server. And of course, Booth has always-on end-to-end encryption of video and audio data: when creating a Booth, a user generates a random secret key in the browser for joining the meeting that can be shared by them with their colleagues – anyone (including the server) without the key cannot eavesdrop on the conversation. (Note that Booth relies on browser support for Insertable Streams/Encoded Transform, which is limited to Chrome-based browsers at this time.) In addition to this end-to-end encryption, Booth also employs additional outer layers of encryption as described in the MPR architecture.
Tuning WebRTC to Protect Users
Browser-based video conferencing services all must use functionality from WebRTC, the browser-based video communication standard. The Interactive Connectivity Establishment (ICE) protocol attempts to establish connectivity between participant(s) and/or server(s) to make WebRTC work.
Like others, Booth uses WebRTC. WebRTC connectivity is established through ICE, which iterates through possible connection pairs to find one that works. Browsers typically implement the ICE protocol themselves, and video conferencing applications build upon this functionality. Browsers will offer their local IP as an candidate that the remote WebRTC target can create possible connection pairs with, to attempt to communicate. However, this default browser behavior leaks metadata to the server. Instead, in Booth we specify a function to filter ICE candidates to remove this metadata before they’re sent to the server.
